1 — Missed Identity Layer
SSI augments the Internet with missed Identity layer that gives a digital identity to a user and provides the user an instrument to share data about himself and others in an end-verifiable way.
2 — It is more philosophical
SSI is #architecture and a set of #principles that build user-centric and data-centric networks where the user has untakable rights to control and access his data and identity without needing centralized organizations or other medium systems. Every network user has the same rights and functions that allow them to manage their data and identity. It is sovereign to you in a network.
3 — The Principles
#Existence — exist in real life
#Control — control their identities.
#Access — access to their data
#Transparency — Systems and algorithms must be transparent.
#Persistence — must be long-lived.
#Portability — identity must be transportable
#Interoperability — Identities should be as widely usable as possible.
#Consent — Users must agree to the use of their identity.
#Minimization — Disclosure of claims must be minimized
#Protection — The rights of users must be protected
4 — Protocols and Open Standards
#Transparency , #Portability, #Interoperability enforced by open standards and portable self-explaining and self contain data format and distributed data with meaning and context understandable for machines and humans. Together with data, we have interoperability of behavior achieved with #protocols that describe data, user roles, and expected behaviors.
5) Full Decoupling of identity, protocols, and data from applications allows the building of entirely decentralized and open-distributed systems for the good of all
5 — Decouple
Full Decoupling of identity, protocols, and data from applications allows the building of entirely decentralized and open-distributed systems for the good of all
6- SSI Tools
SSI tools are like an onion of tools and functions that form your digital identity:
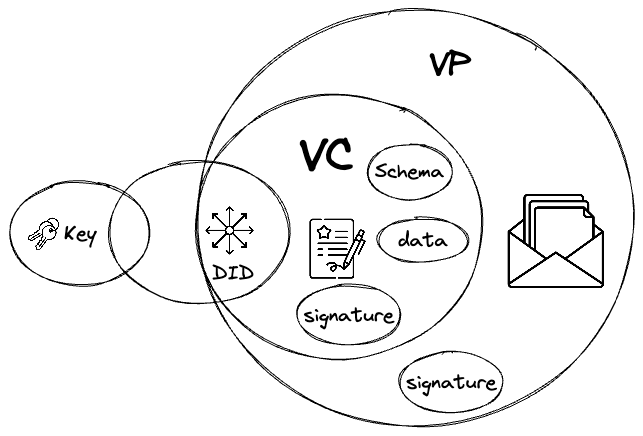
- Asymmetric Keys + Signatures — backbone of decentralized identity in #web3 and #web5 that give #algorithmic #cryptographical basics of identity.
- #DID give Decentralized Public Key Infrastructure that distributes your Public Keys and service endpoints to a broader audience.
- #VC Verifiable credentials allow you to share information about yourself and others in a temper-proof and end-verifiable way. VC contains the issuer’s signature, a person, and an organization that creates a data statement.
- #VP or verifiable presentation solves a problem of proof of Ownership. It is like an envelope with multiple #VC from different issuers or self-issued statements combined with your signature proving your data ownership.
#VP + #DID form your digital identity
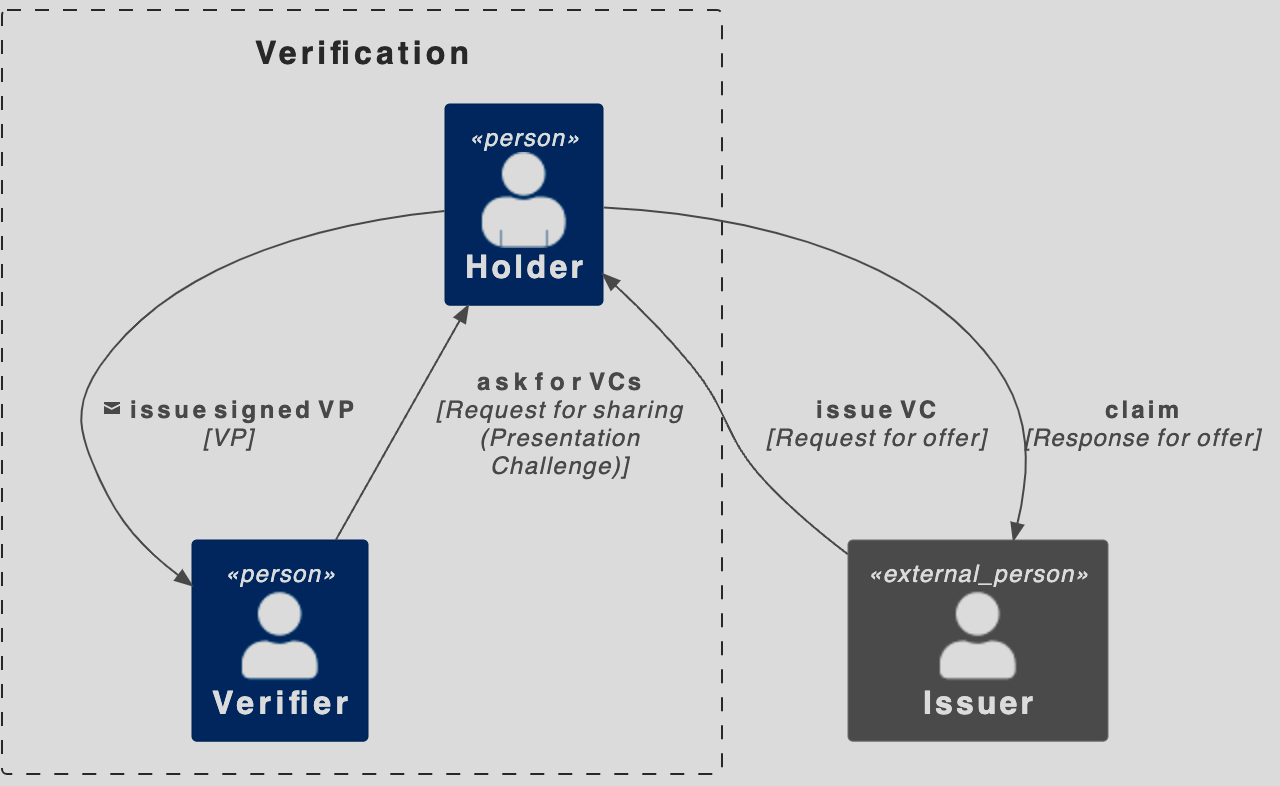
7 — Exchange Protocols and SSI Triangle
#Control , #Consent, #Minimization , #Interoperability enforced by user-centric, exchange protocols. In the scope of these protocols, we have a role:
- holder — a party that owns data and gives content to share data with others via VP
- issuer — party that creates a data point via VC and shares it with a holder
- verifier — attest and check data
Roles are not the permanent user could change roles during the exchange session